Showcasing Coqui (Conditional Keylogger)
DISCLAIMER: This project was made for research purposes. Anything you do with this code is on you and is not my responsibility.
Coqui was originally supposed to be a “banking trojan”, but due to my lack of skills, I settled for a conditional keylogger which only activates when it detects the victim on certain banking sites.
Coqui also contains anti-analysis techniques such as detecting Process Monitor, Process Hacker (anything with Process in the first part of the name, this can also be expanded by adding more conditional statements). If these processes are detected, the main keylogger is opened and overwritten to render analysis of the keylogger useless. The keylogger will also only activate if it detects a banking related window, once that window is out of focus (EX: the user opens calculator), the keylogger is killed.
Once the window monitor starts (ProcKill), it attempts to kill off the keylogger (using system(taskkill /F /T /IM keylogger.exe)) if it doesn’t detect the main window (the window the user is currently working in) being related to anything banking related.
NOTE: It compares a hardcoded list of banking related titles to the current working window, this hardcoded list can be expanded by simply adding in window titles:
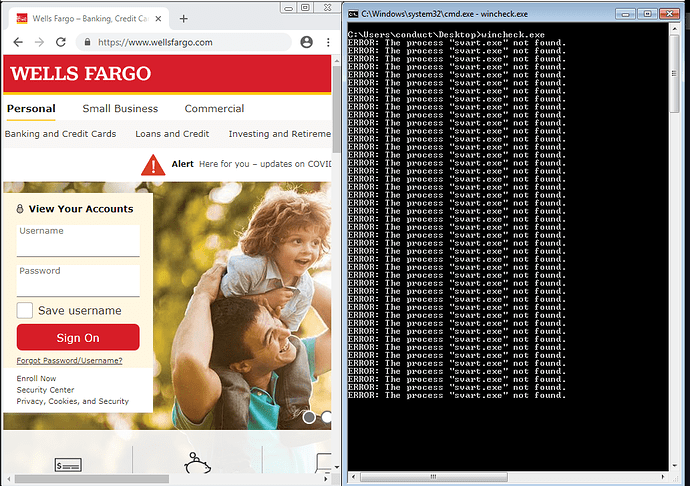
The current working window above is the command prompt, so it attempts to kill off the keylogger (in this case, named svart.exe).
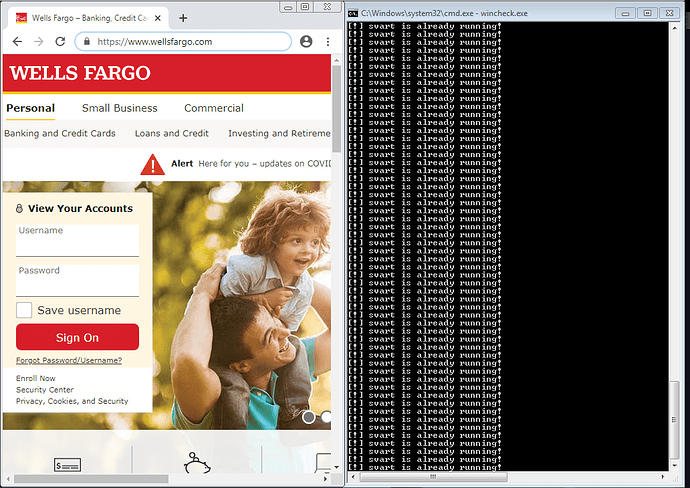
Now, the current window above is the Wells Fargo banking site, so the keylogger is started & ProcKill checks to be sure that it is running before starting it again. If it’s already running, it prints out “[!] svart is already running!”.

If the user changes their current working window & the keylogger is running, we can see the “SUCCESS” message, indicating that the keylogger was killed off due to the user changing windows.
And if a window such as Process Hacker is detected, the keylogger is opened & overwritten, before:
After:

As far as the keylogger goes, it’s fairly basic, the way it exfiltrates the logged data is by sending a GET request to a specified IP address. That IP address should have an Apache server running & logging GET requests. The file dropper.c is responsible for data exfiltration & schedules itself to run every 12 days to exfiltrate the data.
The complete project is hosted on Github for those interested: https://github.com/1d8/Coqui